In this article AJR discuss Locky Ransomware Uses Similarities From Dridex
There’s a new strain of ransomware to be aware of, similar to Dridex, which goes by the name of Locky.
Ransomware is malware which locks files (encrypting them) on the victim’s computer, and demands payment to decrypt them. It’s a threat to both consumers and businesses – and indeed small businesses are increasingly finding themselves the target of cyber-attackers and ransom demands.
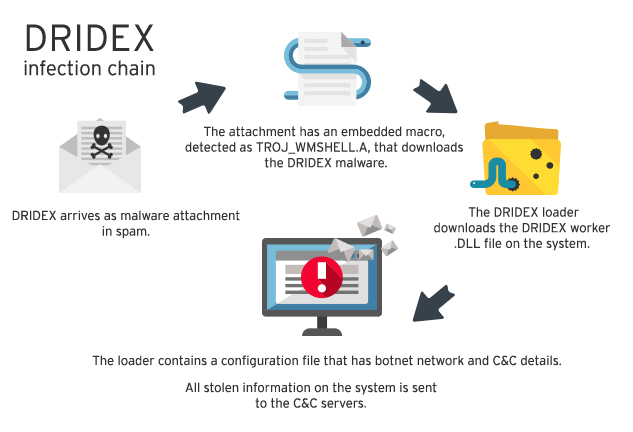
Locky is apparently normally delivered (like Dridex) in a Word document attached to an email, disguised as an invoice that needs a macro. If the document is opened and macros are enabled on the victim’s PC, the ransomware will take hold.
Typically, the subject line of the malicious email will be: “ATTN: Invoice_J-<8-digits>”, where ‘<8-digits>’ is an eight figure number.
As ever, be very careful around any Word attachment you receive no matter what the source. If there’s anything suspicious about the file name or message content, it’s always better to be safe than sorry.
Dridex link
Palo Alto Networks highlighted this threat (as spotted by PC World), and noted: “Researchers suspect there is a link between the Dridex botnet affiliate 220 and Locky due to similar styles of distribution, overlapping filenames, and an absence of campaigns from this particularly aggressive affiliate coinciding with the initial emergence of Locky.”
If this ransomware does hit your machine, it will demand payment in Bitcoins.


